Now that we have come this far, Bucky is now training on Python Sequence and Lists.
EF
Saturday, October 31, 2009
Prevx - PC & Internet Security
Prevx - PC and Internet Security for Home & Families, Businesses, Enterprises, Banks, Financial, eCommerce, and their customers.

Prevx does a great comparison of Anti-Virus vendors by showing the malwares & other that were failed to be detected by AV tools.

Products & Services they offer:

The reason for us talking about Prevx here is because, it would have been a totally new business model for 2001 when Prevx was originally formed. It is an interesting way to compete AV's openly to say how many detection failures has happened during their tests.
This could do one of the following:
(1) Awareness among Prevx viewers:
People who view this comparison chart get an idea of whats missing in each and they could choose one with minimum misses.
(2) Buy Prevx tools:
If Prevx is to the level of finding out what others are lacking, then it generally means that they would make their tools detect stuff, that other tools lack.
(3) Scares the crap out of AV vendors:
Well, it is just a possibility that AV vendors might get scared of their public image and try covering their lack of detection by:
(a) Paying off reality, to cover their weakness from public exposure.
(b) Buying samples/signature or other details of these misses.
(c) Working on fixing their tools, without attempting to contact these vendors.
But in all the above cases(a,b and c) the AV vendors are always on their toes.
This is good business, not just in terms of money but also the way they actually directly or indirectly keep the AV vendors aggressive and alert to protect their business from falling off the cliff.
EF

Prevx does a great comparison of Anti-Virus vendors by showing the malwares & other that were failed to be detected by AV tools.

Products & Services they offer:

The reason for us talking about Prevx here is because, it would have been a totally new business model for 2001 when Prevx was originally formed. It is an interesting way to compete AV's openly to say how many detection failures has happened during their tests.
This could do one of the following:
(1) Awareness among Prevx viewers:
People who view this comparison chart get an idea of whats missing in each and they could choose one with minimum misses.
(2) Buy Prevx tools:
If Prevx is to the level of finding out what others are lacking, then it generally means that they would make their tools detect stuff, that other tools lack.
(3) Scares the crap out of AV vendors:
Well, it is just a possibility that AV vendors might get scared of their public image and try covering their lack of detection by:
(a) Paying off reality, to cover their weakness from public exposure.
(b) Buying samples/signature or other details of these misses.
(c) Working on fixing their tools, without attempting to contact these vendors.
But in all the above cases(a,b and c) the AV vendors are always on their toes.
This is good business, not just in terms of money but also the way they actually directly or indirectly keep the AV vendors aggressive and alert to protect their business from falling off the cliff.
EF
Bucky's Python Programming Tutorial - 7 - More on Strings
More on strings... strings, strings & strings...
Thank you for learning.
EF
Thank you for learning.
EF
Bucky's Python Programming Tutorial - 6 - Strings
Stings and its manipulations on Python.
I think we should start calling these videos as the Bucky's series.
EF
I think we should start calling these videos as the Bucky's series.
EF
Bucky's Python Programming Tutorial - 5 - How to Save Your Programs
Having done, what you have done so far: How do you save your stuff?
Enjoy the video!
EF
Enjoy the video!
EF
Bucky's Python Programming Tutorial - 4 - Modules and Functions
In this video Bucky is talking about functions:
Enjoy the show!
EF
Enjoy the show!
EF
Friday, October 30, 2009
SpyDLLRemover v 2.5 - PortableApps.com Release!
We are glad that Nagareshwar was able to push out a major release for SpyDLLRemover v2.5, we made it into a great release at www.PortableApps.com.

Thanks to PortableApps guys and all the users who suggested very valuable update that made us go for our next major release with Win7 and other upgrades. This would be SpyDLLRemover v 3.0. It is under test phase.
SpyDLLRemover v 3.1 is under planning phase. If you have any features in mind, that you would like to have in SpyDLLRemover, do shoot us an email @ contact.fingers @ gmail.com or leave a comment to this blog. We will definitely consider all entries and respond to the entries even if the chances of implementing it is minimal.
Thank you for everything guys.
EF

Thanks to PortableApps guys and all the users who suggested very valuable update that made us go for our next major release with Win7 and other upgrades. This would be SpyDLLRemover v 3.0. It is under test phase.
SpyDLLRemover v 3.1 is under planning phase. If you have any features in mind, that you would like to have in SpyDLLRemover, do shoot us an email @ contact.fingers @ gmail.com or leave a comment to this blog. We will definitely consider all entries and respond to the entries even if the chances of implementing it is minimal.
Thank you for everything guys.
EF
EFBlog.net - Coming Soon!
EFblog.net is the new EvilFingers Blog. Trying to come up with a new look and feel. We need LAMP and CSS guys for UI and Integrity. If you guys wish to contribute for EvilFingers community, feel free to contact us at any point of time.
Benefits: Knowledge is like fluid, flowing from one to another just like what happens @ EvilFingers. Members share their skills generously, since we believe that the more we share, the more we learn. Do feel free to contact us.
EF
Benefits: Knowledge is like fluid, flowing from one to another just like what happens @ EvilFingers. Members share their skills generously, since we believe that the more we share, the more we learn. Do feel free to contact us.
EF
Python Programming Tutorial - 2 - Numbers and Math
More into numbers[Integer & float] & math on IDLE interpreter.
Thanks for taking your time to check it out.
EF
Thanks for taking your time to check it out.
EF
Python Programming Tutorial - 1 - Installing Python
Python Programming Tutorial - 1 - Installing Python
Bucky from thenewboston channel is offering free python learning videos. If you guys really wanna learn more about python, this video gives you an introduction to installation of Python.
We will check out other tutorial videos that he is offering and start uploading here, one at a time.
EF
Bucky from thenewboston channel is offering free python learning videos. If you guys really wanna learn more about python, this video gives you an introduction to installation of Python.
We will check out other tutorial videos that he is offering and start uploading here, one at a time.
EF
Total Security 2009 Removal Instructions
This video released on Sep 30, 2009. This is great info.
Check it out!
EF
Check it out!
EF
Google's Success: One of the major reasons
When Google was hiring in 1999-2000, I was wondering why they were looking for Algorithm as major focus. They were hiring professionals who were strong with Algorithms, Programming Languages and Computer Architecture, something that I considered as basic stuff when in my college days. But then later, @ some point of time when I got into work, I started finding that foundations are harder to learn than the stuff that comes new.
It is always some new technology or new terminologies that people talk about in many of the community talks or meetings. It is normal to use technical jargon's to show off that someone knows something, but it is very hard to show off that someone knows basics. It is either proven by practical implementation on situations, or even in day to day life when you resolve a situation. Google looks for those kinds of people who are naturally talented in building stuff, destroying barriers and who goes beyond what is required. These are the people who are strong in their foundations. Foundations are most essential when it comes to building something big, especially something as big as Google.
This is one of the major reasons of Google's success. Bravo guys! Really good planning...
EF
It is always some new technology or new terminologies that people talk about in many of the community talks or meetings. It is normal to use technical jargon's to show off that someone knows something, but it is very hard to show off that someone knows basics. It is either proven by practical implementation on situations, or even in day to day life when you resolve a situation. Google looks for those kinds of people who are naturally talented in building stuff, destroying barriers and who goes beyond what is required. These are the people who are strong in their foundations. Foundations are most essential when it comes to building something big, especially something as big as Google.
This is one of the major reasons of Google's success. Bravo guys! Really good planning...
EF
Python Enhancement Proposals[PEP]
Python Enhancement Proposals[PEP] is a list of enhancements written by the Python community. What we love about this is that, they have also written Python Styling a.k.a. coding conventions as a part of the PEP. This structuring looks more like a constitution of the Python Dynasty.
We [EvilFingers] are planning to launch Open Source Initiative[EFOSI] as a part of our tribute to the Python Community. LogsAnalytics[which will be releasing soon] will come with log parsers, log correlation and log analysis tools that would be purely coded in Python and will be open sourced for all our users to get the greater benefit off Python.
Thanks to Guido van Rossum for all of his contributions to the Python world. He works for Google.
EF
We [EvilFingers] are planning to launch Open Source Initiative[EFOSI] as a part of our tribute to the Python Community. LogsAnalytics[which will be releasing soon] will come with log parsers, log correlation and log analysis tools that would be purely coded in Python and will be open sourced for all our users to get the greater benefit off Python.
Thanks to Guido van Rossum for all of his contributions to the Python world. He works for Google.
EF
Mac Users: Here is your Anti-virus
When we talked to some of the Mac users, they asked us if we recommend any good Anti-virus Software for Mac community. Although, we are planning to work on Mac tools, it will certainly take time for us to catch up.
Hence, for now we recommend "iAntiVirus", which is part of PCTools. Here is how it looks:[The following snapshots were taken from http://www.iantivirus.com/screenshots/ and PCTools/iAntiVirus Reserves all the rights]
Update Settings Window:

Settings Window:

Scanner Progress Window:

Quick Scan Window:

Main Window:

If you are interested in full version, you could purchase it at the iAntiVirus site.
If you have any questions or concerns, contact PCTools here.
EF
Hence, for now we recommend "iAntiVirus", which is part of PCTools. Here is how it looks:[The following snapshots were taken from http://www.iantivirus.com/screenshots/ and PCTools/iAntiVirus Reserves all the rights]
Update Settings Window:

Settings Window:

Scanner Progress Window:

Quick Scan Window:

Main Window:

If you are interested in full version, you could purchase it at the iAntiVirus site.
If you have any questions or concerns, contact PCTools here.
EF
Tuesday, October 27, 2009
ZeuS and power Botnet zombie recruitment
As I have said on several occasions, ZeuS botnets is one of the more "media" (hence one of the best known and popular), more aggressive and criminal activity that has more advanced functions that allow phishing attacks, monitor the zombies in real time and collect all this information through different protocols.
These activities primarily aggressive propose methodologies to obtain confidential information from compromised computers for some of the variants that are part of the family ZeuS, now have a wide range of fake pages of banks and financial institutions exclusively for the collection of information through phishing.
Also the possibility of having a monitoring module through which the botmaster can be displayed in real time absolutely everything that is done on the PC zombie (navigation webmail services, banking, online chatting, etc.) poses a serious threat directly undermines confidentiality.
And although many may seem a trivial issue, the mere fact of knowing that your developer updated every version of ZeuS, since 2007, approximately once per month, is an important point that marks the reason for its popularity in the environment under .
But nevertheless, despite all this still doesn't seem to be valued at its true implications are implicit security activities, not only of ZeuS but of any of the alternatives crimeware that daily bombard the Internet with their criminal actions.
Perhaps what follows I will show is a key to understanding the true extent of crime that have this type of activity. This is a botnet ZeuS with a short life span, but with a large amount of zombies that swarm recruited in his headquarters under the tutelage of "dealer" waiting for orders.
The following screenshot shows the zombies recruited only in Russia, in this case by the botmaster logged under the name "russian". This information is obtained through the filtering option, limiting the search with the acronym of the country (UK).
 Now ... one of the questions that perhaps many times we become the talk of botnets is what recruiting is the ability they possess? and although the response is relative might say that has no limits, or that the limit will be given in terms of the capacity of servers used by botmasters.
Now ... one of the questions that perhaps many times we become the talk of botnets is what recruiting is the ability they possess? and although the response is relative might say that has no limits, or that the limit will be given in terms of the capacity of servers used by botmasters.
But, following the example above, we have a sufficiently specific about the power of recruiting has, in this case, the botmaster "russian".
 With an activity of three (3) months with an amount of 24.830 zombies. Something like ZeuS almost 276 infections per day. And if we follow the logic, statistically speaking, the number could quadruple over the year.
With an activity of three (3) months with an amount of 24.830 zombies. Something like ZeuS almost 276 infections per day. And if we follow the logic, statistically speaking, the number could quadruple over the year.
Furthermore, the ability to manage a botnet via web, also means that can be administered several at once, ie several botmasters can use the same web application (in this case ZeuS) to control "their" zombies. Thus, the user "russian" possesses a significant activity. But we can also obtain information from their peers who are managing zombies under the same domain.
For example, the user "system" has recruited 10.184 zombies but over a period of 30 days. Approximately 335 zombies per day. All through a single botnet ZeuS. Can you imagine how many ZeuS how are you are In-the-Wild?
 While less activity botmaster has only 34 zombies, but less than 1 hour.
While less activity botmaster has only 34 zombies, but less than 1 hour.
 In summary, irrespective of length of activity of one or another botnet, the recruitment rate is very high.
In summary, irrespective of length of activity of one or another botnet, the recruitment rate is very high.
This also means that prevention mechanisms aren't sufficiently effective, and indeed a recent study shows clearly that the mechanisms are elusive ZeuS incorporating sufficiently effective against the mechanisms of detection of many current anti-virus solutions.
However, under a more rigorous, current malware self-defense mechanisms incorporate increasingly effective anti-virus doesn't mean that they aren't effective. Furthermore, not all pass through the security solution and much of the responsibility rests with the user and that, ultimately and in accordance with rigorous aspect, a system isn't infected itself.
Related information
ZeuS, spam y certificados SSL
Eficacia de los antivirus frente a ZeuS
Especial!! ZeuS Botnet for Dummies
Botnet. Securización en la nueva versión de ZeuS
Fusión. Un concepto adoptado por el crimeware actual
ZeuS Carding World Template. (...) la cara de la botnet
Entidades financieras en la mira de la botnet Zeus II
Entidades financieras en la mira de la botnet Zeus I
LuckySploit, la mano derecha de Zeus
ZeuS Botnet. Masiva propagación de su troyano II
ZeuS Botnet. Masiva propagación de su troyano I
Jorge Mieres
These activities primarily aggressive propose methodologies to obtain confidential information from compromised computers for some of the variants that are part of the family ZeuS, now have a wide range of fake pages of banks and financial institutions exclusively for the collection of information through phishing.
Also the possibility of having a monitoring module through which the botmaster can be displayed in real time absolutely everything that is done on the PC zombie (navigation webmail services, banking, online chatting, etc.) poses a serious threat directly undermines confidentiality.
And although many may seem a trivial issue, the mere fact of knowing that your developer updated every version of ZeuS, since 2007, approximately once per month, is an important point that marks the reason for its popularity in the environment under .
But nevertheless, despite all this still doesn't seem to be valued at its true implications are implicit security activities, not only of ZeuS but of any of the alternatives crimeware that daily bombard the Internet with their criminal actions.
Perhaps what follows I will show is a key to understanding the true extent of crime that have this type of activity. This is a botnet ZeuS with a short life span, but with a large amount of zombies that swarm recruited in his headquarters under the tutelage of "dealer" waiting for orders.
The following screenshot shows the zombies recruited only in Russia, in this case by the botmaster logged under the name "russian". This information is obtained through the filtering option, limiting the search with the acronym of the country (UK).
 Now ... one of the questions that perhaps many times we become the talk of botnets is what recruiting is the ability they possess? and although the response is relative might say that has no limits, or that the limit will be given in terms of the capacity of servers used by botmasters.
Now ... one of the questions that perhaps many times we become the talk of botnets is what recruiting is the ability they possess? and although the response is relative might say that has no limits, or that the limit will be given in terms of the capacity of servers used by botmasters.But, following the example above, we have a sufficiently specific about the power of recruiting has, in this case, the botmaster "russian".
 With an activity of three (3) months with an amount of 24.830 zombies. Something like ZeuS almost 276 infections per day. And if we follow the logic, statistically speaking, the number could quadruple over the year.
With an activity of three (3) months with an amount of 24.830 zombies. Something like ZeuS almost 276 infections per day. And if we follow the logic, statistically speaking, the number could quadruple over the year.Furthermore, the ability to manage a botnet via web, also means that can be administered several at once, ie several botmasters can use the same web application (in this case ZeuS) to control "their" zombies. Thus, the user "russian" possesses a significant activity. But we can also obtain information from their peers who are managing zombies under the same domain.
For example, the user "system" has recruited 10.184 zombies but over a period of 30 days. Approximately 335 zombies per day. All through a single botnet ZeuS. Can you imagine how many ZeuS how are you are In-the-Wild?
 While less activity botmaster has only 34 zombies, but less than 1 hour.
While less activity botmaster has only 34 zombies, but less than 1 hour. In summary, irrespective of length of activity of one or another botnet, the recruitment rate is very high.
In summary, irrespective of length of activity of one or another botnet, the recruitment rate is very high.This also means that prevention mechanisms aren't sufficiently effective, and indeed a recent study shows clearly that the mechanisms are elusive ZeuS incorporating sufficiently effective against the mechanisms of detection of many current anti-virus solutions.
However, under a more rigorous, current malware self-defense mechanisms incorporate increasingly effective anti-virus doesn't mean that they aren't effective. Furthermore, not all pass through the security solution and much of the responsibility rests with the user and that, ultimately and in accordance with rigorous aspect, a system isn't infected itself.
Related information
ZeuS, spam y certificados SSL
Eficacia de los antivirus frente a ZeuS
Especial!! ZeuS Botnet for Dummies
Botnet. Securización en la nueva versión de ZeuS
Fusión. Un concepto adoptado por el crimeware actual
ZeuS Carding World Template. (...) la cara de la botnet
Entidades financieras en la mira de la botnet Zeus II
Entidades financieras en la mira de la botnet Zeus I
LuckySploit, la mano derecha de Zeus
ZeuS Botnet. Masiva propagación de su troyano II
ZeuS Botnet. Masiva propagación de su troyano I
Jorge Mieres
Sunday, October 25, 2009
What next in Botnets?
For the past few weeks I had been thinking what could be next for Botnets to do C&C. As we have already seen it being having C&C over, IRC in older days, then it came to P2P, and then evolved to HTTP too some time back.
So What next?
Was thinking and thinking and then got it with a flash, how about Simple EMAIL communication is being used as C&C for the bots to receive commands from their bot-masters. That would be mess right, as this would be very difficult to track and stop.
Just think a bot having a bot-masters email ID integrated ( *** there could be more innovative way to have the bot-master ID, I will come to that point latter *** ) and then it calls home just by sending a mail to the bot-master and he responds back by command in the mail body, all encrypted. More over the master need not to run his own C&C server for mails, he could use any of the mail servers available in the internet, like GMail, Yahoo, Hotmail anything he feels like. all bots can respond to those IDs and the bot-master can just issue his commands to all incoming mails from the bots and issue commands, as most of the organizations and client machines will allow mail communication to happen, it will be really tough to stop. There could be more innovative ways to stop being reverse engineering , detection and Bot update mechanism, we all know about it more or less by now, and just think if all those mechanism is integrated, then it could be a big happening in the C&C of botnets.
This is just my thoughts, i am sure people around here in this community may have better thoughts on this concept, I would really appreciate your comments and thoughts on this article and this new future threat, which I think it could be.
All those who agree can please put together your thoughts about some detection mechanism, for this method. And all those who don't agree, I would appreciate to put your line of thoughts too, that will be helpful if i am thinking wrong.
So What next?
Was thinking and thinking and then got it with a flash, how about Simple EMAIL communication is being used as C&C for the bots to receive commands from their bot-masters. That would be mess right, as this would be very difficult to track and stop.
Just think a bot having a bot-masters email ID integrated ( *** there could be more innovative way to have the bot-master ID, I will come to that point latter *** ) and then it calls home just by sending a mail to the bot-master and he responds back by command in the mail body, all encrypted. More over the master need not to run his own C&C server for mails, he could use any of the mail servers available in the internet, like GMail, Yahoo, Hotmail anything he feels like. all bots can respond to those IDs and the bot-master can just issue his commands to all incoming mails from the bots and issue commands, as most of the organizations and client machines will allow mail communication to happen, it will be really tough to stop. There could be more innovative ways to stop being reverse engineering , detection and Bot update mechanism, we all know about it more or less by now, and just think if all those mechanism is integrated, then it could be a big happening in the C&C of botnets.
This is just my thoughts, i am sure people around here in this community may have better thoughts on this concept, I would really appreciate your comments and thoughts on this article and this new future threat, which I think it could be.
All those who agree can please put together your thoughts about some detection mechanism, for this method. And all those who don't agree, I would appreciate to put your line of thoughts too, that will be helpful if i am thinking wrong.
Saturday, October 24, 2009
Portable Apps Release
Thanks to the team and you folks(users), our tool has been released by PortableApps. To check out the portableApps page click here.
Thank you.
EF
Thank you.
EF
Wednesday, October 21, 2009
Metasploit Acquired by Rapid7
For more info, click here.
Rapid7 is a Vulnerability Management company.
**********COPIED AND PASTED FROM HERE*******
**********COPIED AND PASTED FROM HERE*******
For FAQ on this go HERE.
- EF
Rapid7 is a Vulnerability Management company.
**********COPIED AND PASTED FROM HERE*******
Rapid7 Acquired Metasploit
October 21, 2009
I'm extremely pleased to announce Rapid7's acquisition of Metasploit, the leading open source penetration testing framework and world's largest database of public, tested exploits. We believe the acquisition deepens our leadership as the leading provider of vulnerability management, compliance and penetration testing solutions and will provide great value for our customers and partners.
As a result of the acquisition, we will leverage Metasploit technology to enhance our vulnerability management solution, Rapid7 NeXposeTM. At the same time we will not only maintain, but accelerate the open source framework Metasploit with dedicated resources and contributions. I’m also pleased to announce that HD Moore, the founder of Metasploit, will be joining Rapid7 full-time as Chief Architect of Metasploit and Chief Security Officer of Rapid7.
I'm excited about this news for a number of reasons:
The acquisition raises the bar to what our industry can expect from all those involved, be they vendors, end-users, partners or community members. Since joining Rapid7, I’ve learned about some of the key principles of network security: defense in depth, continuously identifying and fixing your vulnerabilities, and improving security through continuous investments in people, process, and technology. With this announcement we are embracing the role of industry innovator by providing better protection to you as our client, feeding the community and creating an environment open for dialog about the implementation of security best practices.
As a result of our union, we will be able to bring superior data on exploitability to our customers, helping them to prioritize and remediate key security issues. The exploit data will be directly embedded in our vulnerability management solution NeXpose, providing a whole new level of risk analysis capabilities to our clients, while ensuring that NeXpose, which will continue as a separate product, delivers the safest, most proactive and actionable vulnerability scanning capabilities in the industry.
We're thrilled that HD Moore and other key Metasploit contributors have joined Rapid7 to work full-time on the open source Metasploit Framework code. HD and the team will now have more dedicated resources and support to invest in exploit research and to create a broader penetration testing platform. As part of our support of the community, we will contribute vulnerability data from the NeXpose product to expand the accuracy and reliability of the Metasploit Framework, which will remain open source. It is a true win-win for everyone.
Finally, the combination of NeXpose and Metasploit will enable Rapid7 to continue to grow its relationship with partners and consultants, delivering improved technology and more comprehensive solutions for vulnerability management and penetration testing. Having a broader portfolio will further accelerate our dialog with our partner ecosystem to ensure that our solutions meet their needs.
Over the next weeks we will be providing additional details on our plans so please stay tuned to hear more from us. For additional information, please reference our press release on the acquisition as well as the FAQ below. If you have any feedback or suggestions regarding our announcement, I would love to hear from you.
Mike Tuchen,
President & CEO, Rapid7
**********COPIED AND PASTED FROM HERE*******
For FAQ on this go HERE.
- EF
Computer Weekly IT Blog Awards 2009
Computer Weekly is coming up with the IT Blog Awards 2009. Thanks to Kalyan for sending a reminder email. We have enrolled "EvilFingers Blog" in the nominees. If you think that we are good for this award, kindly VOTE for us.
EF
EF
Sunday, October 18, 2009
Current business outlook caused by crimeware
Undoubtedly, the current picture of global criminal activities that are channeled through the web form a round, dark business that is happening in the most underground of the different environments of the Internet, stealing private information through different "bugs"...
 ...that spread running different "plans" strategically designed, including developing applications to automate processes that are marketed criminal in the same environment underground, then transform everything into cash.
...that spread running different "plans" strategically designed, including developing applications to automate processes that are marketed criminal in the same environment underground, then transform everything into cash.
Without further ado ... image sums it up :)
Related information
CYBINT en el negocio de los ciber-delincuentes rusos
Software as a Service en la industria del malware
Los precios del crimeware ruso. Parte 2
Los precios del crimeware ruso. Parte 1
Comercio Ruso de versiones privadas de crimeware...
Automatización de procesos anti-análisis II
Jorge Mieres
 ...that spread running different "plans" strategically designed, including developing applications to automate processes that are marketed criminal in the same environment underground, then transform everything into cash.
...that spread running different "plans" strategically designed, including developing applications to automate processes that are marketed criminal in the same environment underground, then transform everything into cash.Without further ado ... image sums it up :)
Related information
CYBINT en el negocio de los ciber-delincuentes rusos
Software as a Service en la industria del malware
Los precios del crimeware ruso. Parte 2
Los precios del crimeware ruso. Parte 1
Comercio Ruso de versiones privadas de crimeware...
Automatización de procesos anti-análisis II
Jorge Mieres
Saturday, October 17, 2009
A recent tour of scareware XVI
Advanced Virus Remover
 MD5: b3f4e680db0b4093737093afc5bd7ddd
MD5: b3f4e680db0b4093737093afc5bd7ddd
IP: 92.241.177.207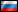
Dominios asociados
1-vscodec-pro.com
10-open-davinci.com
advanced-virus-remover-2009.com
advanced-virus-remover2009.com
advanced-virusremover2009.com
advancedvirus-remover-2009.com
 antivirus-2009-ppro.com
antivirus-2009-ppro.com
antivirus-scan-2009.com
best-scanpc.com
bestscanpc.com
bestscanpc.info
bestscanpc.net
blue-xxx-tube.com
downloadavr3.com
downloadavr4.com
onlinescanxppro.com
testavrdown.com
trucountme.com
vscodec-pro.com
Result: 21/41 (51.22%)
securitycentr.com (195.24.78.186), webscannertools.com (212.117.165.126) -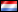
antivir-freescan.com/online (213.163.64.81) -
computervirusscanner31.com/scan1 (213.163.89.60) -
benharpergals.com/?pid=162&sid=c3d08e (89.248.174.61) -
iniegox.cn/installer.1.exe (91.213.29.250) -
avidentify.com (91.206.201.8) -
scan.helpyourpcsecuritynow.com/download/smrtprt/install.php (195.95.151.185) -
goxtrascan.com (91.212.107.103) -
virushooker.com (206.53.61.73) -
fastscansearch.net (64.86.16.101), globalscansearch.com (64.86.16.130), totalscansearch.com (64.86.16.100), totalscansearch.net (64.86.16.124) -
securitycodereviews.com/install/ws.exe, bestwebsitesecurity.com (62.90.136.237) -
weedruk.com/download (91.212.127.132) -
mycompscanner42.com (206.217.201.240), myvirusscanner2.com (206.217.201.136) -
myvirusscanner25.com/2 (69.4.230.204) -
fp.outerinfo.com/dispatcher.php, outerinfo.com (63.251.135.18) -
block-spyware.co.cc/htm6.exe (78.46.129.170) -
safefighter.com (83.233.30.66) -
keymydomains.com (193.169.12.26) -
trustsoldier.com (212.175.87.195) -
Perfect Defender 2009
 IP: 206.161.120.40
IP: 206.161.120.40
 United States Herndon Beyond The Network America Inc
United States Herndon Beyond The Network America Inc
Dominios asociados
agelesscommunity.com, air-titaniumusa.com, alcohol-treatmentcenter.com, antigreen.org, arkansasrobotics.com, barry-miller.com, brianperez.com, cocainedrugtreatment.com, combat-camera.com, pcfender.com, pcfsupport.com
PC MightyMax
 MD5: e630ee28e264d060562cb567e7fa5ed0
MD5: e630ee28e264d060562cb567e7fa5ed0
IP: 208.38.128.164
 United States Valrico Sonbry Marking International
United States Valrico Sonbry Marking International
Dominios asociados
pc-mm.com
pcmightymax.net
dllfix.net
pc-test.com
pcmightymax.net
Result: 1/41 (2.44%)
Nortel Antivirus
 IP: 174.142.96.6
IP: 174.142.96.6
 Canada Montreal Iweb Technologies Inc
Canada Montreal Iweb Technologies Inc
Dominios asociados
nortel-antivirus-pro.com
nortel2010.com
Screen-Spy
 MD5: 21b5e0a17c057a281b6e7a90c3f8ce7a
MD5: 21b5e0a17c057a281b6e7a90c3f8ce7a
IP: 208.109.106.46
 United States Scottsdale Godaddy.com Inc
United States Scottsdale Godaddy.com Inc
Dominios asociados
logserver39.com, acespy.com, pchealthoptimizer.com, retinaxstudios.com, screen-spy.com, loanmodcrm.org
Result: 17/41 (41.46%)
SaferScan
 MD5: cb9022235cc4ae3adc9f54cd49b81bf5
MD5: cb9022235cc4ae3adc9f54cd49b81bf5
IP: 66.152.93.119
 Canada Integrated Search Technologies
Canada Integrated Search Technologies
Dominios asociados
activexcash.net, instaldownload.com, installcash.com, power-scan.com, safer-scan.com, sexsearchbar.com, toolbarcash.com,
unlimitedsongs.net, xxxtoolbar.com
Result: 23/41 (56.10%)
Información relacionada
Una recorrida por los últimos scareware XV
Una recorrida por los últimos scareware XIV
Una recorrida por los últimos scareware XIII
Una recorrida por los últimos scareware XII
Una recorrida por los últimos scareware XI
Una recorrida por los últimos scareware X
Una recorrida por los últimos scareware IX
Una recorrida por los últimos scareware VIII
Una recorrida por los últimos scareware VII
Una recorrida por los últimos scareware VI
Una recorrida por los últimos scareware V
Una recorrida por los últimos scareware IV
Una recorrida por los últimos scareware III
Una recorrida por los últimos scareware II
Una recorrida por los últimos scareware I
Jorge Mieres
 MD5: b3f4e680db0b4093737093afc5bd7ddd
MD5: b3f4e680db0b4093737093afc5bd7dddIP: 92.241.177.207
Dominios asociados
1-vscodec-pro.com
10-open-davinci.com
advanced-virus-remover-2009.com
advanced-virus-remover2009.com
advanced-virusremover2009.com
advancedvirus-remover-2009.com
 antivirus-2009-ppro.com
antivirus-2009-ppro.comantivirus-scan-2009.com
best-scanpc.com
bestscanpc.com
bestscanpc.info
bestscanpc.net
blue-xxx-tube.com
downloadavr3.com
downloadavr4.com
onlinescanxppro.com
testavrdown.com
trucountme.com
vscodec-pro.com
Result: 21/41 (51.22%)
securitycentr.com (195.24.78.186), webscannertools.com (212.117.165.126) -
antivir-freescan.com/online (213.163.64.81) -
computervirusscanner31.com/scan1 (213.163.89.60) -
benharpergals.com/?pid=162&sid=c3d08e (89.248.174.61) -
iniegox.cn/installer.1.exe (91.213.29.250) -
avidentify.com (91.206.201.8) -
scan.helpyourpcsecuritynow.com/download/smrtprt/install.php (195.95.151.185) -
goxtrascan.com (91.212.107.103) -
virushooker.com (206.53.61.73) -
fastscansearch.net (64.86.16.101), globalscansearch.com (64.86.16.130), totalscansearch.com (64.86.16.100), totalscansearch.net (64.86.16.124) -
securitycodereviews.com/install/ws.exe, bestwebsitesecurity.com (62.90.136.237) -
weedruk.com/download (91.212.127.132) -
mycompscanner42.com (206.217.201.240), myvirusscanner2.com (206.217.201.136) -
myvirusscanner25.com/2 (69.4.230.204) -
fp.outerinfo.com/dispatcher.php, outerinfo.com (63.251.135.18) -
block-spyware.co.cc/htm6.exe (78.46.129.170) -
safefighter.com (83.233.30.66) -
keymydomains.com (193.169.12.26) -
trustsoldier.com (212.175.87.195) -
Perfect Defender 2009
 IP: 206.161.120.40
IP: 206.161.120.40Dominios asociados
agelesscommunity.com, air-titaniumusa.com, alcohol-treatmentcenter.com, antigreen.org, arkansasrobotics.com, barry-miller.com, brianperez.com, cocainedrugtreatment.com, combat-camera.com, pcfender.com, pcfsupport.com
PC MightyMax
 MD5: e630ee28e264d060562cb567e7fa5ed0
MD5: e630ee28e264d060562cb567e7fa5ed0IP: 208.38.128.164
Dominios asociados
pc-mm.com
pcmightymax.net
dllfix.net
pc-test.com
pcmightymax.net
Result: 1/41 (2.44%)
Nortel Antivirus
 IP: 174.142.96.6
IP: 174.142.96.6Dominios asociados
nortel-antivirus-pro.com
nortel2010.com
Screen-Spy
 MD5: 21b5e0a17c057a281b6e7a90c3f8ce7a
MD5: 21b5e0a17c057a281b6e7a90c3f8ce7aIP: 208.109.106.46
Dominios asociados
logserver39.com, acespy.com, pchealthoptimizer.com, retinaxstudios.com, screen-spy.com, loanmodcrm.org
Result: 17/41 (41.46%)
SaferScan
 MD5: cb9022235cc4ae3adc9f54cd49b81bf5
MD5: cb9022235cc4ae3adc9f54cd49b81bf5IP: 66.152.93.119
Dominios asociados
activexcash.net, instaldownload.com, installcash.com, power-scan.com, safer-scan.com, sexsearchbar.com, toolbarcash.com,
unlimitedsongs.net, xxxtoolbar.com
Result: 23/41 (56.10%)
Información relacionada
Una recorrida por los últimos scareware XV
Una recorrida por los últimos scareware XIV
Una recorrida por los últimos scareware XIII
Una recorrida por los últimos scareware XII
Una recorrida por los últimos scareware XI
Una recorrida por los últimos scareware X
Una recorrida por los últimos scareware IX
Una recorrida por los últimos scareware VIII
Una recorrida por los últimos scareware VII
Una recorrida por los últimos scareware VI
Una recorrida por los últimos scareware V
Una recorrida por los últimos scareware IV
Una recorrida por los últimos scareware III
Una recorrida por los últimos scareware II
Una recorrida por los últimos scareware I
Jorge Mieres
Friday, October 16, 2009
15 day summary - SANS - Cyber Security Awareness Month
This is a great initiative taken by SANS.
Day 15 - Ports 995, 465, and 993 - Secure Email
Day 14 - port 514 - syslog
Day 13 - Proxies (TCP 3128, 8080 & ......)
Day 12 - Ports 161/162 Simple Network Management Protocol (SNMP)
Day 11 - RPCBind aka Portmapper
Day 10 - The Questionable Ports
Day 09 - Port 3389/tcp (RDP)
Day 08 - Port 25 - SMTP
Day 07 - Port 6667/8/9/7000 - IRC: is it evil?
Day 06 - ports 67&68 udp - bootp and dhcp
Day 05 - port 31337
Day 04 - Port 20/21 - FTP-data/FTP
Day 03 - Port 5900 - VNC
Day 02 - Port 0
Day 01 - Port 445 - SMB over TCP
It is really good to have someone/team, talking about valuable stuff that not many others think about.
Good work Sans!
- EF
Day 15 - Ports 995, 465, and 993 - Secure Email
Day 14 - port 514 - syslog
Day 13 - Proxies (TCP 3128, 8080 & ......)
Day 12 - Ports 161/162 Simple Network Management Protocol (SNMP)
Day 11 - RPCBind aka Portmapper
Day 10 - The Questionable Ports
Day 09 - Port 3389/tcp (RDP)
Day 08 - Port 25 - SMTP
Day 07 - Port 6667/8/9/7000 - IRC: is it evil?
Day 06 - ports 67&68 udp - bootp and dhcp
Day 05 - port 31337
Day 04 - Port 20/21 - FTP-data/FTP
Day 03 - Port 5900 - VNC
Day 02 - Port 0
Day 01 - Port 445 - SMB over TCP
It is really good to have someone/team, talking about valuable stuff that not many others think about.
Good work Sans!
- EF
SpyDLLRemover - 10,000 downloads from RootkitAnalytics.com
Hello folks,
Just noticed that we reached 10,000 downloads for SpyDLLRemover from the main site, RootkitAnalytics.com.
PortableApps.com is now releasing SpyDLLRemover among their Security Suite of tools next week. The test release is here.
Thank you for your support guys.
- EF
Just noticed that we reached 10,000 downloads for SpyDLLRemover from the main site, RootkitAnalytics.com.
PortableApps.com is now releasing SpyDLLRemover among their Security Suite of tools next week. The test release is here.
Thank you for your support guys.
- EF
Book of the Month - "The Art of Assembly Language"
The Art of Assembly Language

Chapter Listings:
This book deserved an applause for its:
Thank you Randall Hyde - For sharing your skills in this book, and Thanks to NoStarch press for publishing it.
You can buy it at NoStarch Press, as both PDF and/or Paper copy.
- EF

Chapter Listings:
Contents
Chapter 1 : Hello,World of Assembly Language
Chapter 2 : Data Representation
Chapter 3 : Memory Access and Organization
Chapter 4 : Constants, Variables and Data Types
Chapter 5 : Procedures and Units
Chapter 6 : Arithmetic
Chapter 7 : Low Level Control Structures
Chapter 8 : Files
Chapter 9 : Advanced Arithmetic
Chapter 10: Macros and the HLA Compile Time Language
Chapter 11: Bit Manipulation
Chapter 12: The String Instructions
Chapter 13: The MMX Instruction Set
Chapter 14: Classes and Objects
Chapter 15: Mixed Language Programming
Appendix A: ASCII Character Set
Appendix B: The 80x86 Instruction Set
Index
This book deserved an applause for its:
Structural flow
Language [simplicity]
Overall content coverage
Thank you Randall Hyde - For sharing your skills in this book, and Thanks to NoStarch press for publishing it.
You can buy it at NoStarch Press, as both PDF and/or Paper copy.
- EF
Operating System Engineering - Assembly Language - MIT Materials
Assembly Language programming links to several free materials available at Operating System Engineering course.
References page has reference to all the following materials:
Really Good Stuff.
- EF
References page has reference to all the following materials:
Selection of Operating System Papers
Available on the 6.828 schedule.
UNIX
* The UNIX Time-Sharing System, Dennis M. Ritchie and Ken L.Thompson,. Bell System Technical Journal 57, number 6, part 2 (July-August 1978) pages 1905-1930. (local copy) You read this paper in 6.033.
* The Evolution of the Unix Time-sharing System, Dennis M. Ritchie, 1979.
* The C programming language (second edition) by Kernighan and Ritchie. Prentice Hall, Inc., 1988. ISBN 0-13-110362-8, 1998.
x86 Emulation
* QEMU - A fast and popular x86 platform and CPU emulator.
o User manual
* Bochs - A more mature, but quirkier and much slower x86 emulator. Bochs is generally a more faithful emulator of real hardware than QMEU.
o User manual
o Debugger reference
x86 Assembly Language
* PC Assembly Language, Paul A. Carter, November 2003. (local copy)
* Intel 80386 Programmer's Reference Manual, 1987 (HTML). (local copy - PDF) (local copy - HTML)
Much shorter than the full current Intel Architecture manuals below, but describes all processor features used in 6.828.
* IA-32 Intel Architecture Software Developer's Manuals, Intel, 2007. Local copies:
o Volume I: Basic Architecture
o Volume 2A: Instruction Set Reference, A-M
o Volume 2B: Instruction Set Reference, N-Z
o Volume 3A: System Programming Guide, Part 1
o Volume 3B: System Programming Guide, Part 2
* Multiprocessor references:
o MP specification
o IO APIC
* AMD64 Architecture Programmer's Manual.
Covers both the "classic" 32-bit x86 architecture and the new 64-bit extensions supported by the latest AMD and Intel processors.
* Writing inline assembly language with GCC:
o Brennan's Guide to Inline Assembly, Brennan "Mr. Wacko" Underwood
o Inline assembly for x86 in Linux, Bharata B. Rao, IBM
o GCC-Inline-Assembly-HOWTO, Sandeep.S
* Loading x86 executables in the ELF format:
o Tool Interface Standard (TIS) Executable and Linking Format (ELF).
The definitive standard for the ELF format.
PC Hardware Programming
* General PC architecture information
o Phil Storrs PC Hardware book, Phil Storrs, December 1998.
o Bochs technical hardware specifications directory.
* General BIOS and PC bootstrap
o BIOS Services and Software Interrupts, Roger Morgan, 1997.
o "El Torito" Bootable CD-ROM Format Specification, Phoenix/IBM, January 1995.
* VGA display - kern/console.c
o VESA BIOS Extension (VBE) 3.0, Video Electronics Standards Association, September 1998. (local copy)
o VGADOC, Finn Thøgersen, 2000. (local copy - text) (local copy - ZIP)
o Free VGA Project, J.D. Neal, 1998.
* Keyboard and Mouse - kern/console.c
o Adam Chapweske's resources.
* 8253/8254 Programmable Interval Timer (PIT) - inc/timerreg.h
o 82C54 CHMOS Programmable Interval Timer, Intel, October 1994. (local copy)
o Data Solutions 8253/8254 Tutorial, Data Solutions.
* 8259/8259A Programmable Interrupt Controller (PIC) - kern/picirq.*
o 8259A Programmable Interrupt Controller, Intel, December 1988.
* Real-Time Clock (RTC) - kern/kclock.*
o Phil Storrs PC Hardware book, Phil Storrs, December 1998. In particular:
+ Understanding the CMOS
+ A list of what is in the CMOS
o CMOS Memory Map, Padgett Peterson, May 1996.
o M48T86 PC Real-Time Clock, ST Microelectronics, April 2004. (local copy)
* 16550 UART Serial Port - kern/console.c
o PC16550D Universal Asynchronous Receiver/Transmitter with FIFOs, National Semiconductor, 1995.
o Technical Data on 16550, Byterunner Technologies.
o Interfacing the Serial / RS232 Port, Craig Peacock, August 2001.
* IEEE 1284 Parallel Port - kern/console.c
o Parallel Port Central, Jan Axelson.
o Parallel Port Background, Warp Nine Engineering.
o IEEE 1284 - Updating the PC Parallel Port, National Instruments.
o Interfacing the Standard Parallel Port, Craig Peacock, August 2001.
* IDE hard drive controller - fs/ide.c
o AT Attachment with Packet Interface - 6 (working draft), ANSI, December 2001.
o Programming Interface for Bus Master IDE Controller, Brad Hosler, Intel, May 1994.
o The Guide to ATA/ATAPI documentation, Constantine Sapuntzakis, January 2002.
* Sound cards (not supported in 6.828 kernel, but you're welcome to do it as a challenge problem!)
o Sound Blaster Series Hardware Programming Guide, Creative Technology, 1996.
o 8237A High Performance Programmable DMA Controller, Intel, September 1993.
o Sound Blaster 16 Programming Document, Ethan Brodsky, June 1997.
o Sound Programming, Inverse Reality.
* E100 Network Interface Card
o Intel 8255x 10/100 Mbps Ethernet Controller Family Open Source Software Developer Manual
o 82559ER Fast Ethernet PCI Controller Datasheet
o The 82559 EEPROM
Really Good Stuff.
- EF
ZDNET: Does software piracy lead to higher malware infection rates?
Does software piracy lead to higher malware infection rates? - Very nice posting... something to think about...
Does this mean open-source software is better off, since we could see the code. But even if the code is provided, can all the end users understand whats on the code? Freeware could also be infected, since the code ain't open. The only solution that we could think of, is to certify all the software downloads before them getting downloaded. Which means, that someone would be or would have already written an application for that. But, would that application also be malicious, would that application also bring in malware? Who knows...
The answer always is "It Depends..."
- EF
Does this mean open-source software is better off, since we could see the code. But even if the code is provided, can all the end users understand whats on the code? Freeware could also be infected, since the code ain't open. The only solution that we could think of, is to certify all the software downloads before them getting downloaded. Which means, that someone would be or would have already written an application for that. But, would that application also be malicious, would that application also bring in malware? Who knows...
The answer always is "It Depends..."
- EF
Saturday, October 10, 2009
Level of (im)maturity in prevention
A few days ago I received an email (not arrived as spam) that I am attracted wide attention, so I wanted to know its origin. Here you can see a screenshot of the email.
 This is a false message intentionally sent to my email. The first thing that crossed my mind to see it was, first, the memory of the old "xploits" he thought, mistakenly, missing the fact only because it's easy to underestimate them and their condition very crude attempt to deceive users, on the other, questions will be effective ... today?, what's the level of preventing users from this sort of cheating?
This is a false message intentionally sent to my email. The first thing that crossed my mind to see it was, first, the memory of the old "xploits" he thought, mistakenly, missing the fact only because it's easy to underestimate them and their condition very crude attempt to deceive users, on the other, questions will be effective ... today?, what's the level of preventing users from this sort of cheating?
The point is that I also wanted to know their origins. And so I came up a website that offers the "service", specifically, to send this sort of cheating with several alternatives regarding the strategies employed. And of course ... actually, not that the "xploits" ceased to exist but they changed their nomenclature, as this is nothing to Phishing.
 However, before dealing in more detail some features of this site, I'd like to share some of the arguments expressed by the author directly through the "terms of use." The first thing we read is welcome ...
However, before dealing in more detail some features of this site, I'd like to share some of the arguments expressed by the author directly through the "terms of use." The first thing we read is welcome ...
"Interested to discover passwords of friends, boyfriends/as, heads, enemies/as of who you want? You know that getting the password of your victim could get many things as personal data, data access and personal sites plenty of information."
This type of activity is punishable in most countries since the mail has the character of private ... condoning the crime? Besides ... someone wants to access my email account :)
It continues with some thingsfunny curious that I share... "All the information provided here is for educational use and/or science."
"Scientific use?... without words...
"Our software is not designed to be used for malevolent purposes, the product was intended for responsible adults, not every person under age 18 may use our programs."
However, to access the site doesn't display a warning stating that they can only access the site over 18 years...
"Spyware programs were created as a solution for remote monitoring and surveillance of the computer."
From the perspective in which information security discusses these aspects, is nothing but an act framed in the guise of privacy violation. There are alternative, less intrusive and aggressive for the purposes of parents who want to "monitor" certain activities of their children without coming to an abusive state. In this regard I consider the best solution is useless if not accompanied by education regarding the dangers that exist online. The question isn't spying on our children...
Aside from the superficial to the mechanism of deception, the domain is hosted at Hosting Solutions International Inc, located in the U.S. under the IP address 69.64.58.50. At least three domains are in this direction and all redirected to the same page.
When you access this "service", we find a menu which is managed by the maneuvers of deception, allowing sending emails with fake messages to the main services (real) webmail and two of the most popular social networks. Even you can customize the messages.
 The procedure, after selecting the service option to be used to provide a consistent level of confidence is a matter of selecting one option among several. As an example, consider a snapshot of a Gmail account bombarded with an example of each.
The procedure, after selecting the service option to be used to provide a consistent level of confidence is a matter of selecting one option among several. As an example, consider a snapshot of a Gmail account bombarded with an example of each.
 All contain in the body of the message, that address links to a fake page, in this case of Gmail, which requests an authentication process that is part of the deception. The page is a clone of the real and you are looking to steal user's authentication data to the webmail service. But according to this, the question is ... how do realize that is false?
All contain in the body of the message, that address links to a fake page, in this case of Gmail, which requests an authentication process that is part of the deception. The page is a clone of the real and you are looking to steal user's authentication data to the webmail service. But according to this, the question is ... how do realize that is false?
Mainly, checking where to redirect the links found in the message. With the mere fact of passing the mouse over the link in the taskbar is the actual address.
Likewise, we must check the URL. In this case, the address begins with http://login.live.1d8gfh35f9h6438d2g6.tumsg.com/accounts/ServiceLogin.php?service false...
While the real beginning with
https://www.google.com/accounts/ServiceLogin?service...
Besides being completely different, false doesn't have the secure protocol (https) characteristic of all sites that require authentication via the web. While this particular aspect doesn't guarantee full security is a good habit to check your existence.
However, suppose that the attack is directed to a Hotmail user. The real address for this is:
http://login.live.com/login.srf?wa=wsignin1.0&rpsnv=11&ct=1255052408&rver=6.0.5285.0&wp=MBI&wreply=http:%2F%2Fmail.live.com%2fdefault.aspx&lc=3082&id=64855&mkt=en-
In this case we aren't with "https" and the false address is very similar to the real, which, it's likely that a user who doesn't understand much about it, fall into the trap without too much effort, but wonder... How many users verify the address?
Now, try to find some answers to the questions discussed above lines (are they effective now?, What is the level of preventing users from this sort of cheating?)
To obtain a test that was done was basically sending emails with fake messages using the "services" offered by this website, obviously under strict ethical sense as the intention is only investigative. Moreover, unless they pay a minimum cost of USD 15, there is no access to passwords.
What the business makes it evident that behind this system of deception. Also at the same time, its creators are made from a large database which until now has over 95.000 records, where each of those records is a victim.
For our purposes, obtain a statistic of the level of maturity in terms of sense of prevention on users, but passwords don't need to know how many users rely on the false message.
The sample consisted of 100 addresses to which it sent the same message that had come to my email. From one day to another, ie within 24 hours, emails sent Hundred, these were the results:
Sent: 100
User who fell into the trap: 12
 As we see, a little over 10% of users who received this email with the message you have opened, and not only that, but have also offering trusted him unknowingly credentials data access to your accounts e-mail.
As we see, a little over 10% of users who received this email with the message you have opened, and not only that, but have also offering trusted him unknowingly credentials data access to your accounts e-mail.
Accordingly, trivial attacks of this kind are more common than people think and have a worrisome level of effectiveness, but more worrying still is, in a way, that the level of maturity in terms of prevention is still low and that if these values are enhanced depending on the amount of emails of this kind that any spammer could send per day, the final death toll is very high.
Related information
Estado de la seguridad según Microsoft
Phishing y "cuentos" en navidad
Phishing para American Express y consejos
Jorge Mieres
 This is a false message intentionally sent to my email. The first thing that crossed my mind to see it was, first, the memory of the old "xploits" he thought, mistakenly, missing the fact only because it's easy to underestimate them and their condition very crude attempt to deceive users, on the other, questions will be effective ... today?, what's the level of preventing users from this sort of cheating?
This is a false message intentionally sent to my email. The first thing that crossed my mind to see it was, first, the memory of the old "xploits" he thought, mistakenly, missing the fact only because it's easy to underestimate them and their condition very crude attempt to deceive users, on the other, questions will be effective ... today?, what's the level of preventing users from this sort of cheating?The point is that I also wanted to know their origins. And so I came up a website that offers the "service", specifically, to send this sort of cheating with several alternatives regarding the strategies employed. And of course ... actually, not that the "xploits" ceased to exist but they changed their nomenclature, as this is nothing to Phishing.
 However, before dealing in more detail some features of this site, I'd like to share some of the arguments expressed by the author directly through the "terms of use." The first thing we read is welcome ...
However, before dealing in more detail some features of this site, I'd like to share some of the arguments expressed by the author directly through the "terms of use." The first thing we read is welcome ..."Interested to discover passwords of friends, boyfriends/as, heads, enemies/as of who you want? You know that getting the password of your victim could get many things as personal data, data access and personal sites plenty of information."
This type of activity is punishable in most countries since the mail has the character of private ... condoning the crime? Besides ... someone wants to access my email account :)
It continues with some things
"Scientific use?... without words...
"Our software is not designed to be used for malevolent purposes, the product was intended for responsible adults, not every person under age 18 may use our programs."
However, to access the site doesn't display a warning stating that they can only access the site over 18 years...
"Spyware programs were created as a solution for remote monitoring and surveillance of the computer."
From the perspective in which information security discusses these aspects, is nothing but an act framed in the guise of privacy violation. There are alternative, less intrusive and aggressive for the purposes of parents who want to "monitor" certain activities of their children without coming to an abusive state. In this regard I consider the best solution is useless if not accompanied by education regarding the dangers that exist online. The question isn't spying on our children...
Aside from the superficial to the mechanism of deception, the domain is hosted at Hosting Solutions International Inc, located in the U.S. under the IP address 69.64.58.50. At least three domains are in this direction and all redirected to the same page.
When you access this "service", we find a menu which is managed by the maneuvers of deception, allowing sending emails with fake messages to the main services (real) webmail and two of the most popular social networks. Even you can customize the messages.
 The procedure, after selecting the service option to be used to provide a consistent level of confidence is a matter of selecting one option among several. As an example, consider a snapshot of a Gmail account bombarded with an example of each.
The procedure, after selecting the service option to be used to provide a consistent level of confidence is a matter of selecting one option among several. As an example, consider a snapshot of a Gmail account bombarded with an example of each. All contain in the body of the message, that address links to a fake page, in this case of Gmail, which requests an authentication process that is part of the deception. The page is a clone of the real and you are looking to steal user's authentication data to the webmail service. But according to this, the question is ... how do realize that is false?
All contain in the body of the message, that address links to a fake page, in this case of Gmail, which requests an authentication process that is part of the deception. The page is a clone of the real and you are looking to steal user's authentication data to the webmail service. But according to this, the question is ... how do realize that is false?Mainly, checking where to redirect the links found in the message. With the mere fact of passing the mouse over the link in the taskbar is the actual address.
Likewise, we must check the URL. In this case, the address begins with http://login.live.1d8gfh35f9h6438d2g6.tumsg.com/accounts/ServiceLogin.php?service false...
While the real beginning with
https://www.google.com/accounts/ServiceLogin?service...
Besides being completely different, false doesn't have the secure protocol (https) characteristic of all sites that require authentication via the web. While this particular aspect doesn't guarantee full security is a good habit to check your existence.
However, suppose that the attack is directed to a Hotmail user. The real address for this is:
http://login.live.com/login.srf?wa=wsignin1.0&rpsnv=11&ct=1255052408&rver=6.0.5285.0&wp=MBI&wreply=http:%2F%2Fmail.live.com%2fdefault.aspx&lc=3082&id=64855&mkt=en-
In this case we aren't with "https" and the false address is very similar to the real, which, it's likely that a user who doesn't understand much about it, fall into the trap without too much effort, but wonder... How many users verify the address?
Now, try to find some answers to the questions discussed above lines (are they effective now?, What is the level of preventing users from this sort of cheating?)
To obtain a test that was done was basically sending emails with fake messages using the "services" offered by this website, obviously under strict ethical sense as the intention is only investigative. Moreover, unless they pay a minimum cost of USD 15, there is no access to passwords.
What the business makes it evident that behind this system of deception. Also at the same time, its creators are made from a large database which until now has over 95.000 records, where each of those records is a victim.
For our purposes, obtain a statistic of the level of maturity in terms of sense of prevention on users, but passwords don't need to know how many users rely on the false message.
The sample consisted of 100 addresses to which it sent the same message that had come to my email. From one day to another, ie within 24 hours, emails sent Hundred, these were the results:
Sent: 100
User who fell into the trap: 12
 As we see, a little over 10% of users who received this email with the message you have opened, and not only that, but have also offering trusted him unknowingly credentials data access to your accounts e-mail.
As we see, a little over 10% of users who received this email with the message you have opened, and not only that, but have also offering trusted him unknowingly credentials data access to your accounts e-mail.Accordingly, trivial attacks of this kind are more common than people think and have a worrisome level of effectiveness, but more worrying still is, in a way, that the level of maturity in terms of prevention is still low and that if these values are enhanced depending on the amount of emails of this kind that any spammer could send per day, the final death toll is very high.
Related information
Estado de la seguridad según Microsoft
Phishing y "cuentos" en navidad
Phishing para American Express y consejos
Jorge Mieres
Subscribe to:
Comments (Atom)
